Spurred on by the rapid advance of digitalisation, trends and changes, far-reaching implications are emerging in industrial communication. Open communication and the ever-stronger networking of production systems not only offer huge opportunities, but also a major risk of being hit by a cyber attack.Security Integrated network components from Siemens, such as SCALANCE S Industrial Security , SCALANCE M Internet and mobile wireless routers, can be added for protected and simultaneously practical remote access to widespread machinery and plants.
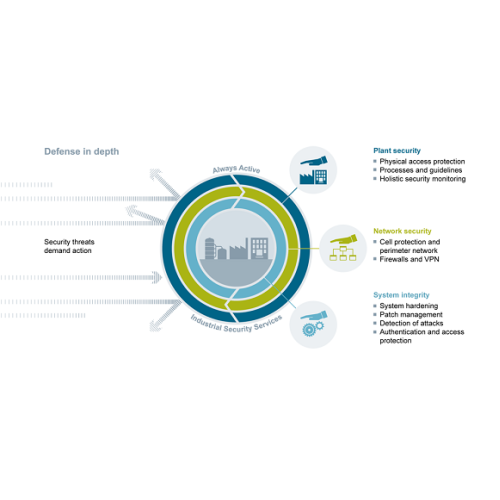

Digitalization and the growing networking of machines and industrial systems also mean an increase in the risk of cyberattacks. Appropriate protective measures are imperative, especially for critical infrastructure facilities. An approach that covers all levels simultaneously – from the operational to the field level and from access control to copy protection – is essential for comprehensively protecting industrial facilities against internal and external cyberattacks.
Did you know, we are an entrusted Siemens approved partner?
All goods supplied by us are sold upon the following conditions. This agreement applies as between you, the User of this Web Site or Purchaser and Parmley Graham Limited the owner(s) of this Web Site. Your agreement to comply with and be bound by these Terms and Conditions is deemed to occur upon your first use of the Web Site. If you do not agree to be bound by these Terms and Conditions, you should stop using the Web Site immediately. No part of this Web Site is intended to constitute a contractual offer capable of acceptance. The Purchaser's order constitutes a contractual offer and our acceptance of that offer is deemed to occur upon our sending an email to the Purchaser indicating that the order has been accepted for processing. Unless expressly agreed by us in writing, any other terms or conditions, including any which may be contained in your orders, are excluded. Unless expressly incorporated in our quotation or tender, all descriptions, illustrations, drawings, dimensions, weights, measures, specifications, standards of performance or other descriptive matter of precontractual statement are approximate only and shall not form part of the contract.
These Terms and Conditions apply to business customers only.
If Goods are being ordered from outside Parmley Graham Limited's country of residence, import duties and taxes may be incurred once the Goods reach their destination. Parmley Graham Limited is not responsible for these charges and we undertake to make no calculations or estimates in this regard. If a Purchaser is buying internationally, they are advised to contact their local customs authorities for further details on costs and procedures. The Purchaser of the Goods will also be the importer of record and as such should ensure that the purchase is in full compliance with the laws of the country into which the Goods are being imported. Please be aware that Goods may be inspected on arrival at port for customs purposes and Parmley Graham Limited gives no guarantee that the packaging of the Goods will be free of signs of tampering.
Any such order placed via our website will be considered to be an “Invitation to Treat” and any payment made as a refundable deposit, until such time as the order is reviewed and confirmed. During our contract review we are legally obliged to take into account any Export Restrictions, Sanctions or Embargoes in force at the time from the UK Government, European Union or UN ( US export regulations may also apply to some products) and such restrictions may prevent supply of the goods. In some cases we may require End-User details and/or Dual Use WMD statements prior to supply. Should an Export License be required, or additional documentation including Certificates of Origin, it may be necessary to apply additional costs.
In order to purchase Goods on this Web Site and to use the other facilities Users are required to create an Account which will contain certain personal details and Payment Information which may vary based upon a User's use of the Web Site as we may not require payment information until a purchase is to be made. By continuing to use this Web Site you represent and warrant that:
All information you submit is accurate and truthful;
If you are buying on behalf of your employers, you have the authority to submit Payment Information where any such authority is required; and
You will keep this information accurate and up-to-date. Your creation of an Account is further affirmation of your representation and warranty.
It is recommended that you do not share your Account details, particularly your username and password. Parmley Graham Limited accepts no liability for any losses or damages incurred as a result of your Account details being shared by you. If you use a shared computer, it is recommended that you do not save your Account details in your internet browser. If you have reason to believe that your Account details have been obtained by another without consent, you should contact Parmley Graham Limited immediately to suspend your Account and cancel any unauthorised purchases that may be pending. Please be aware that purchases can only be cancelled until they are dispatched. In the event that an unauthorised purchase is dispatched prior to your notifying us of the unauthorised nature of the purchase, Parmley Graham Limited accepts no liability or responsibility and you should make contact with the Carrier detailed in the Purchase Information.
All goods are sold subject to the prices ruling at the date of despatch.
The price of the Goods shall be subject to the addition of the applicable delivery prices as indicated on the Web Site, Value Added Tax and other applicable taxes and the cost of any special packing required by the Customer.
A small order charge may be applied to orders less than £25 (ex VAT).
Payment must be made by the 28th day of the month subsequent to the month following delivery on a "Strictly Net" basis. We shall be entitled to charge interest on overdue accounts at the rate of 1.5% per month. (b) Where the contract is to be or may be fulfilled in separate installments deliveries or parts, payment for each such installment, delivery or part shall be made as if the same constituted a separate contract.
The risk in all goods passes to you when they first enter the premises stipulated on the order. We reserve the right to choose the method of transport, to charge for deliveries, and charge you with manufacturers' carriage charges for special items.
The Company may deliver the Goods in instalments and invoice the Customer as if each instalment comprised a separate Contract upon the terms of these Conditions.
Notification of any shortage or damage must be received at our branch within seven days after the date of delivery; otherwise no claim will be entertained. Written notice of any non delivery must be received at our branch within seven days after the date of invoice. Time is of the essence of this clause. Our liability in respect of any claim accepted under this clause is limited to making up the shortage or replacing any goods proven to have been damaged or lost in transit to the point of delivery, and we accept no liability for any loss or damage suffered by you whether direct or consequential and howsoever arising.
Any delivery dates quoted by the Company are approximate only and will not form part of the contract. Stock indications are provided on the Web Site; however these may not take into account sales that have taken place during your visit to the web site. If the customer fails for whatever reason to take delivery of the goods on the due date the Company will be entitled to store the goods and then risk in the goods will pass to the customer, delivery will be deemed to have taken place and the customer will pay all costs and expenses including storage and insurance charges arising from its failure.
Notwithstanding delivery, all goods supplied by us will remain our absolute property until you pay in full for them and for all other goods previously supplied by us. You will store the goods in such a way that they are readily identifiable as our property, but you may, as trustees for us, sell them to a third party in the normal course of your business. Upon any sale by you of the goods (either alone or with other items) all rights which you have against the buyer shall automatically vest in us. We shall be entitled immediately after giving notice of our intention to repossess, to enter upon any premises with such transport as may be necessary and repossess any goods to which we have title under this clause.
It is your responsibility to determine that the goods are sufficient and suitable for the purpose to which they are to be put. We cannot accept any responsibility either in respect of the installation of any goods or as to the ultimate performance of any product in which the goods may be installed. We shall in no way be liable for any direct or consequential damage, loss or expense arising from any defect or inefficiency caused by the manner in which the goods are used.
All goods supplied by us are manufactured by others. Accordingly, we shall pass on to you the benefit of the warranty, if any, given by the manufacturer of the goods. Our liability under this clause shall be in lieu of any warranty or condition implied by law as to the quality or fitness for any particular purpose of the goods, and we shall not be under any liability, whether in contract, tort or otherwise, in respect of any defects in goods delivered or for any injury, damage or loss resulting from such defects or from anything done or omitted in connection with the goods or from any work done in connection therewith.
In no circumstances may goods supplied against a firm order be returned without our prior written consent and the receipt of your advice note stating the reason for return and date and number of our invoice. All goods returned must be securely packed and consigned carriage paid. In all cases we reserve the right to make a handling charge, and the issue of our goods received note will not bind us to issue any credit in respect of the goods.
We may, without prejudice to our other rights and remedies determine the contract or any unfulfilled part of it or withhold further deliveries or make partial deliveries if: (a) You fail to make payment on the due date under this or any other contract between us. (b) You purport to cancel or suspend, or commit any breach of this or any other contract between us. (c) You become insolvent, or make any composition with your creditors or have a receiver appointed of all or any part of your undertaking or assets or go into liquidation (save for the purposes of amalgamation or reconstruction) and we shall be entitled to recover from you all our loss including any loss of profit or loss on resale.
Any failure by us to enforce any of all these Conditions shall not be construed as a waiver of any of our rights hereunder.
The information contained in this website is for general information purposes only. The information is provided by Parmley Graham Limited and whilst we endeavour to keep the information up-to-date and correct, we make no representations or warranties of any kind, express or implied, about the completeness, accuracy, reliability, suitability or availability with respect to the website or the information, products, services, or related graphics contained on the website for any purpose. Any reliance you place on such information is therefore strictly at your own risk.
In no event will we be liable for any loss or damage including without limitation, indirect or consequential loss or damage, or any loss or damage whatsoever arising from loss of data or profits arising out of or in connection with the use of this website
Every effort is made to keep the website up and running smoothly. However, Parmley Graham Limited takes no responsibility for and will not be liable for the website being temporarily unavailable due to technical issues beyond our control.
Data controller: Parmley Graham Limited,
South Shore Road, Gateshead, Tyne and Wear, NE8 3AE
Parmley Graham Limited collects and processes your personal data when you interact with us. For the purposes of this Privacy Policy, references to “we”, “us” or “the organisation” shall refer to Parmley Graham Limited. The organisation is the data controller of your personal data and is responsible for complying with data protection laws. The organisation is committed to being transparent about how it collects and uses that data and to meeting its data protection obligations.
This notice applies to all suppliers, customers and other parties who utilise the services of Parmley Graham Limited.
By providing your personal data, you acknowledge that we may use it only in the ways set out in this Privacy Policy.
From time to time we may need to make changes to this Privacy Policy, for example as the result of government regulation, new technologies, or other developments in data protection laws or privacy generally and will provide you with a new privacy notice when we make substantial updates.
Our privacy principles
When we collect and use your personal data, we ensure we look after it properly and use it in accordance with our privacy principles below whereby the personal information we hold about you must be:
· processed fairly and lawfully and in a transparent way;
· obtained only for specific, lawful purposes;
· adequate, relevant and not excessive;
· accurate and kept up to date;
· not held for any longer than necessary;
· processed in accordance with the rights of data subjects;
· protected in appropriate ways;
· not be transferred outside the European Economic Area (EEA), unless where necessary and that country or territory also ensures an adequate level of protection.
What personal data do we collect?
We collect and process a range of data about you. This may include:
· contact details such as name, email address, postal address and telephone number;
· financial information and information about the nature of your business, such as bank details, credit card details and information obtained as a result of our credit checks;
· details of your interactions with us through our branches or online;
· information about the nature of your business and commercial assets;
· your image may be recorded on CCTV when you visit a Parmley Graham site;
· information obtained through our use of cookies. You can find out more about this in our cookies policy; and
· your marketing preferences.
How do we collect your personal data?
We collect, store and process personal data directly from you:
· via enquiry;
· when you create an account with us;
· when you purchase any of our products or services;
· through quotes;
· via our telephone calls with you;
· via emails;
· when you provide your details to us either online or offline;
· when you engage with us on social media;
How do we use your personal data?
We mainly use your personal data to provide you with goods and services. There are a number of other reasons we use your personal data, as explained in the list below.
In specific situations we require your data to pursue our legitimate interests in a way which might reasonably be expected as part of running our business, whilst ensuring that such business needs do not interfere with your rights and freedoms and do not cause you any harm. Where we list legitimate interests as a reason, we also describe below what we believe these legitimate interests are.
In specific situations, we can collect and process your data with your consent. We will usually only ask for your consent when providing marketing information to you, including information about other products and services. This will be made clear when you provide your personal information. If we ask for your consent we will explain why it is necessary.
|
What we use your personal data for |
Our reasons (legal basis) |
Explanation of our legitimate interests |
|
Set up your customer account |
Legitimate interest |
Process efficiency in dealing with such activity |
|
Provide you with quotes |
Legitimate interest |
Process efficiency in dealing with such activity |
|
Process your order, to supply you with goods and services |
Contractual obligation |
Fulfil the contract |
|
Notify you of your order status |
Legitimate interest |
Process efficiency in dealing with such activity |
|
Manage your account |
Legitimate interest |
Maintaining our business records |
|
Detect, investigate and report financial crime (eg Fraud) |
Legal compliance |
NA |
|
Undertake marketing communication, to inform you about other products and services |
Legitimate interest |
To keep subscribed customers up to date with information on related services and products. |
|
The use of CCTV to record images for security. |
Legitimate interest |
To protect our customers, premises, assets and employees from crime |
Who has access to the data?
Your information may be shared internally within the organisation, including with the Directors, members of the HQ finance team, IT staff and branch employees if access to the data is necessary for performance of their roles.
Also, we may sometimes share your data with trusted third parties that process the data on our behalf. We share only the personal information they need to perform their specific services and they may only use your data for the reasons we’ve described.
We work closely with the third party data processors to ensure your privacy is respected and protected at all times.
How do we protect the data?
The organisation takes the security of your data seriously. We have internal policies and controls in place to try to ensure that your data is not lost, accidentally destroyed, misused or disclosed, and is not accessed except by its employees in the performance of their duties.
We secure access to our systems and access to your personal data is password protected.
We regularly monitor our system for possible vulnerabilities and attacks, and we carry out penetration testing to identify ways to further strengthen security.
We work closely with the third party data processors to ensure your privacy is respected and protected at all times.
For how long do we keep the data?
We will only retain your personal data for as long as is necessary to fulfil the purposes for which it is collected.
When assessing what retention period is appropriate for your personal data, we take into consideration:
· the requirements of our business and the services provided;
· any statutory or legal obligations;
· the purposes for which we originally collected the personal data;
· the lawful grounds on which we based our processing;
· the types of personal data we have collected;
· the amount and categories of your personal data; and
· whether the purpose of the processing could reasonably be fulfilled by other means.
Your duty to inform us of changes
It is important that the personal information we hold about you is accurate and current. Please keep us informed if your personal information changes during your working relationship with us.
Your rights / contacting the regulator
As a data subject, you have the following rights in relation to our use of your personal data:
- The right to access your personal data
You are entitled to a copy of the personal data we hold about you and certain details of how we use it
- The right to rectification
We take reasonable steps to ensure that the personal information we hold about you is accurate and complete. However, if you do not believe this is the case, please contact us by using the details shown in your documentation and you can ask us to update or amend it.
- The right to erasure
In certain circumstances, you have the right to ask us to erase your personal information, for example where the personal information we collected is no longer necessary for the original purpose or where you withdraw your consent. However, this will need to be balanced against other factors, for example according to the type of personal information we hold about you and why we have collected it, there may be some legal and regulatory obligations which mean we cannot comply with your request.
- The right to restriction of processing
In certain circumstances, you are entitled to ask us to stop using your personal information, for example where you think that the personal information we hold about you may be inaccurate or where you think that we no longer need to process your personal information.
- The right to data portability
In certain circumstances, you have the right to ask that we transfer any personal information that you have provided to us to another third party of your choice. Once transferred, the other party will be responsible for looking after your personal information.
- The right to object to direct marketing
You can ask us to stop sending you marketing messages at any time. Please see the Marketing section at the end of this page for more information.
- The right not to be subject to automated decision-making
We do not use automated decision-making
- The right to withdraw consent
For certain uses of your personal information, we will ask for your consent. Where we do this, you have the right to withdraw your consent to further use of your personal information.
If you would like to exercise any of these rights, please contact email: privacy@parmley-graham.co.uk, address: Parmley Graham Ltd, South Shore Road, Gateshead, Tyne and Wear, NE8 3AE.
If we choose not to action your request we will explain to you the reasons for our refusal.
If you feel that your data has not been handled correctly, or you are unhappy with our response to any requests you have made to us regarding the use of your personal data, you have the right to lodge a complaint with the Information Commissioner’s Office.
You can contact them by calling 0303 123 1113.
Or go online to https://ico.org.uk/make-a-complaint/ (opens in a new window; please note we can't be responsible for the content of external websites)
If you are based outside the UK, you have the right to lodge your complaint with the relevant data protection regulator in your country of residence.
Marketing
We are committed to only sending you marketing communications that you have clearly expressed an interest in receiving. If you wish to unsubscribe from emails sent by us, you may do so at any time by following the unsubscribe instructions that appear in all emails or by sending an email, from the email address you wish to have unsubscribed, to unsubscribe@parmley-graham.co.uk.
Date of last review: 23/05/2024
